Difference between revisions of "Zentyal"
From Blue-IT.org Wiki
(→Using hooks) |
(→Using hooks) |
||
| Line 69: | Line 69: | ||
=== Using hooks === | === Using hooks === | ||
| − | When the firewall module of Zentyal is restarted, all iptable-rules (see [[NAT]]) will be reset. So it is wise to use teh zentyal hook system to reset the desired rules! See section [[Zentyal#Customization Customization]] | + | When the firewall module of Zentyal is restarted, all iptable-rules (see [[NAT]]) will be reset. So it is wise to use teh zentyal hook system to reset the desired rules! See section [[Zentyal#Customization|Customization]] |
=== LDAP port changed on Zentyal 3.2 === | === LDAP port changed on Zentyal 3.2 === | ||
Revision as of 20:32, 2 November 2013
Zentyal - the small business server for Linux
- http://wiki.ubuntuusers.de/Zentyal
- http://wiki.ubuntuusers.de/Zentyal/PPA-Installation
- http://ubuntuserverguide.com/2012/11/how-to-instal-zentyal-3-0-on-ubuntu-server-12-04-lts.html
Base installation on ubuntu 12.04 LTS
We are startigng with a bare ubuntu system with only ssh enabled.
First of all please update all packages and do some configurations:
vim /etc/apt/sources.list
Uncomment the following line:
deb http://archive.canonical.com/ubuntu precise partner
We install the apt-add-repository-script to be able to use the zentyal repository afterwards and do a full system upgrade:
apt-get install -y python-software-properties apt-add-repository ppa:zentyal/3.0 apt-get update apt-get dist-upgrade apt-get clean
Then add an administrative account for zentyal.
To be able to access the webinterface you have setup an administrativ user which belongs to the admin group. This is NOT the ubuntu adm group! You have to create the group first:
groupadd admin useradd myAdmin passwd myAdmin usermod -G admin -a myAdmin ...
Pleas verify, that the newly created user is part of the new group with:
su my Admin groups
Finally reboot the system:
reboot
Install Zentyal
The base system then will be install via the command
apt-get -y install zentyal
This will install all prerequisites. Please prepare to have:
- the or a mysql root password
- the port for the webinterface
I suggest 444 for the webinterface, so it would not be in conflict with https-pages on your site (you can then access the webinterface via http://vserver:444).
Configure the services
You will now be able to access the webinterface via http://vserver:444.
There choose the services you like. It is always good, of possible to to a snapshot after each of this steps and test, if everything went ok!
Firewall
IMPORTANT: Alter your firewall settings to enable the Zentyal administration !!!
Otherwise you won't be able to access the webinterface.
In case you forget this you can temporaryly disable the firewall via commandline and alter this settings.
/etc/init.d/zentyal firewall stop
Using hooks
When the firewall module of Zentyal is restarted, all iptable-rules (see NAT) will be reset. So it is wise to use teh zentyal hook system to reset the desired rules! See section Customization
LDAP port changed on Zentyal 3.2
By default LDAP uses the port 389. The problem is, that samba4 - which is part of Zentyal 3.2 - already uses this port.
For that reason LDAP on Zentyal 3.x is running on port 390. This is not documented on the first sight, and in the firewall, the "LDAP" is assigned to prot 389.
Solution:
- add a custom port 390 and name it e.g. LDAP-Zentyal
- open the port in the firewall for the internal network traffice (or outside, which is NOT wise)
Test with. Replace <ZENTYAL-SERVER-IP> with the IP of your LDAP-server
ldapsearch -x -p 390 -LLL -h <ZENTYAL-SERVER-IP> -b "" -s base "(objectclass=*)" supportedSASLMechanisms
LDAP
[Update] --Apos (talk) 11:06, 2 November 2013 (CET)
This is tested with Zentyal 3.2 on Ubuntu 12.04 LTS and Redmine 2.3.3-2 (via ppa). ! Be aware and read the section LDAP port changed on Zentyal 3.2 !
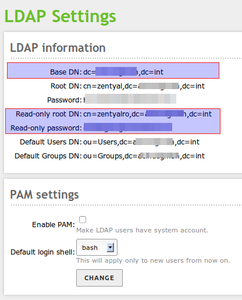
On the users and group-page in the zentyal administration page there are the credentials you need to get readonly access to LDAP.
LDAP credentials in zentyal:
Basedomain (Base DN): dc=your_domain,dc=your_tld Rootdomain (Root DN): cn=zentyal,dc=your_domain,dc=your_tld Password: <admin_secret_pass> Read-only root DN: cn=zentyalro,dc=your_domain,dc=your_tld Read-only password: <ro_secret_pass> Default Users DN: ou=Users,dc=your_domain,dc=your_tld Default Groups DN: ou=Groups,dc=your_domain,dc=your_tld
For testing, if you have the right credential, you can use e.g. the free and opensource JXplorer or the commandline:
Check if, the server accepts incoming port
telnet <IP_OF_LDAP_SERVER> 390
ldapsearch -x -p 390 -b "<Basedomain (Base DN)>" -h <IP_OF_LDAP_SERVER> \ -D "<Read-only root DN>" -w "<Read-only password>"
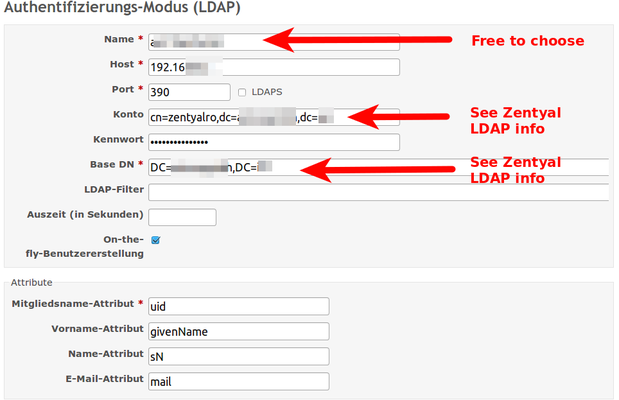
Figured that out, you can e.g. use LDAP in Redmine like this:
Network
Zentyal completely cares for the network on your ubuntu server.
Therefore you should - but do not have to - disable the network-manager:
sudo service network-manager stop
Create an override file for the upstart job:
echo "manual" | sudo tee /etc/init/network-manager.override
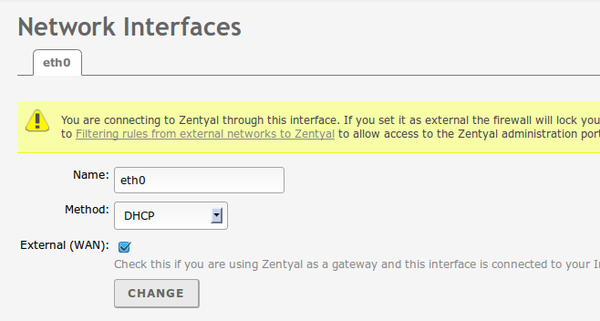
Then configure your network cards with zentyal and be sure to enable the WAN switch, if you are using zentyal on an internetserver without a gateway in front of it, that is, if your server ip is an internet ip address:
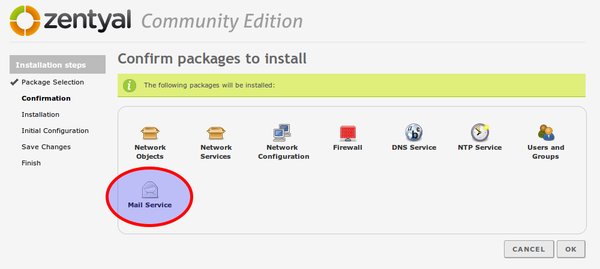
First of all we like to install an e-mail-system. This is what most users want, when they install zentyal on an vserver.
If you only choose the mail plugin, several plugins will be installed, too:
In the next steps, it is important that you
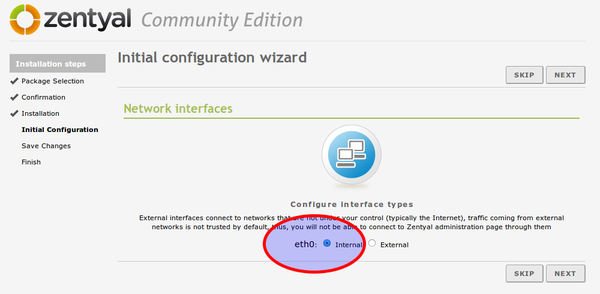
- choose eth0 as interface (see picture) and later
- DHCP for the configuration of eth0.
- Directly afterwards you will be asked for the Kerberos REALM. Please use the domain name of your server, if configured. If not SKIP this step for now!
Virtualisation module moved
Like advised here ...
... some of the modules - especially the virtualisation module - have moved to a so called contribution section.
- [...]
- Moreover, as announced in the Forum, the following modules have been moved to the contrib repositories in order to live
- up to our motto of being an easy-to-use Linux small business server:
- * PPTP
- * Virtualization
- * Thin clients
- * VoIP
- [...]
A solution can be found here:
Samba4 - changing the REALM
Sometimes it can be necessary to alter the realm (kerberos). This will brake all user related modules and forces them to reinstall:
/usr/share/zentyal-users/reinstall
- Then klick on the "Ally"-Button on the upper right corner of the web-interface.
- Then go to "Users" -> "Mode...", change the realm and apply.
- Then you have to reenable the "Users"-module and apply the changes.
- Then you can also reenable the "Samba"-module and apply the changes.