Difference between revisions of "NAT"
From Blue-IT.org Wiki
(Created page with "=== Bug in Ubuntu for accessing virtual machines behind a bridge === On ubuntu 12.04 there is a [https://bugs.launchpad.net/ubuntu/+source/procps/+bug/50093 Ubuntu bug #50093]...") |
|||
| Line 83: | Line 83: | ||
done | done | ||
fi | fi | ||
| + | |||
| + | [Category:Virtualisation] | ||
| + | [Category:Network] | ||
| + | [Category:KVM] | ||
| + | [Category:Security] | ||
Revision as of 17:24, 1 November 2013
Bug in Ubuntu for accessing virtual machines behind a bridge
On ubuntu 12.04 there is a Ubuntu bug #50093 (mentioned here) which prevents accessing a machine inside the bridges network:
> vim /etc/sysctl.conf net.bridge.bridge-nf-call-ip6tables = 0 net.bridge.bridge-nf-call-iptables = 0 net.bridge.bridge-nf-call-arptables = 0
Acitvate
sysctl -p /etc/sysctl.conf
Make permanent
> vim /etc/rc.local *** Sample rc.local file *** /sbin/sysctl -p /etc/sysctl.conf iptables -A FORWARD -p tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu exit 0
Verify
tail /proc/sys/net/bridge/*
iptables -L FORWARD
> brctl show
bridge name bridge id STP enabled interfaces
br1 8000.50e5492d616d no eth1
vnet1
[...]
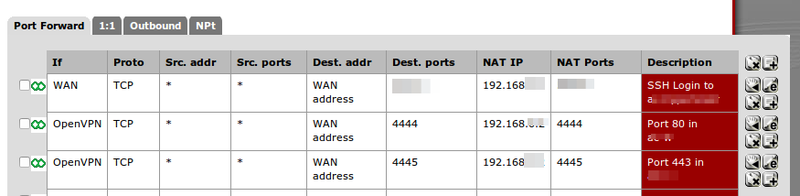
Accessing ports in servers behind a natted bridge and firewall
Be careful. By doing this, you open up ports to the outside world. If you are using pfSense in front of your host or another firewall you can simply restrict this by using VPN.
Access from internet to guest:
internet -> pfSense (WAN / host ip and port)
-> host port -> iptables -> nat bridge -> guest port
Access only via vpn to guest
internet -> pfSense (OpenVPN / host ip and port)
-> host port -> iptables -> nat bridge -> guest port
Use the next script ...
Bash script for setting ip tables
To add a rule
set_iptables add
To remove it
set_iptables remove
> vim ~/bin/set_iptables
#!/bin/bash
if [ ${1} = "" ]
then
echo "Usage with either 'add' or 'remove' ... RETRY"
exit 1
fi
# the virtual hosts adress
Guest_ipaddr=192.168.0.3
Host_port=( '4444' '4445' )
Guest_port=( '80' '443' )
length=$(( ${#Host_port[@]} - 1 ))
if [ "${1}" = "remove" ]; then
for i in $(seq 0 $length); do
iptables -t nat -D PREROUTING -p tcp --dport ${Host_port[$i]} -j DNAT \
--to ${Guest_ipaddr}:${Guest_port[$i]}
iptables -D FORWARD -d ${Guest_ipaddr}/32 -p tcp -m state --state NEW \
-m tcp --dport ${Guest_port[$i]} -j ACCEPT
done
fi
if [ "${1}" = "add" ]; then
for i in `seq 0 $length`; do
iptables -t nat -A PREROUTING -p tcp --dport ${Host_port[$i]} -j DNAT \
--to ${Guest_ipaddr}:${Guest_port[$i]}
iptables -I FORWARD -d ${Guest_ipaddr}/32 -p tcp -m state --state NEW \
-m tcp --dport ${Guest_port[$i]} -j ACCEPT
done
fi
[Category:Virtualisation] [Category:Network] [Category:KVM] [Category:Security]