Difference between revisions of "Zentyal"
From Blue-IT.org Wiki
(Created page with "== Changing the REALM == Needs to restart all user related modules: /usr/share/zentyal-users/reinstall see: http://trac.zentyal.org/ticket/5695 Category: Zentyal") |
(→Secure the Webinterface with an ssh tunnel) |
||
| (126 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | == | + | = Zentyal - the small business server for Linux = |
| + | ===Important links === | ||
| + | * http://wiki.ubuntuusers.de/Zentyal | ||
| + | * http://wiki.ubuntuusers.de/Zentyal/PPA-Installation | ||
| + | * http://ubuntuserverguide.com/2012/11/how-to-instal-zentyal-3-0-on-ubuntu-server-12-04-lts.html | ||
| + | == Installation and Upgrading to Ubuntu 14.04 LTS == | ||
| + | === HowTo === | ||
| + | * http://www.tecmint.com/install-zentyal-as-primary-domain-controller-and-integrate-windows-system/ | ||
| + | Unfortunately Zentyal changed it's release policy DRAMATICALLY since Version 3.4 (3.5). | ||
| − | + | * See and carfully read: [http://www.zentyal.org/zentyal-release-policy Zentyal Release Policy]. | |
| + | * [http://www.zentyal.org/roadmap/zentyal-3-3-roadmap 3.3 roadmap] | ||
| + | * [http://www.zentyal.org/roadmap/zentyal-3-4-roadmap 3.4 roadmap] | ||
| + | * [http://www.zentyal.org/roadmap/zentyal-4-0-roadmap 4.0 roadmap] | ||
| + | |||
| + | Nur die kommerziellen Versionen Zentyal folgen den Ubuntu-LTS Fahrplan und bieten entsprechende Migrationswege und Werkzeuge an! | ||
| + | |||
| + | |||
| + | '''Be very carful on updating an existing Ubuntu 12.04 LTS Zentyal installation.''' | ||
| + | |||
| + | You will most probably loose a lot of important functionality! | ||
| + | |||
| + | Read carfully and check the new requirements at http://www.zentyal.org/zentyal-release-policy | ||
| + | |||
| + | It in fact boils down that '''you loose on update''': | ||
| + | |||
| + | * '''Zarafa module''' (!) - and thereby your mail configuration an installation which ist WORST! | ||
| + | * '''Webserver configuration module''' - you have to manage it manually. This is not very dramatic. | ||
| + | * Be aware and prepared of '''apache2.4 versus apache 2.2''' config changes (which mainly you can read about in [[Webserver#Apache_2.4]]). | ||
| + | * '''Radius''' - which in my case is crucial, since almost any service relys on this for authentification! | ||
| + | |||
| + | |||
| + | New is: | ||
| + | |||
| + | * Openchange support - which is very PROMISING | ||
| + | * You'll get an '''Rolling Release''' - that means updating Zentyal almost ever need updating the server to a new Ubuntu version which could probably lead to strange side effects for other mission critical systems (database server, programming language environments like ruby) ... | ||
| + | |||
| + | === A personal comment on this === | ||
| + | As far as I can say, the new release policy of Zentyal is very annoying on the first place. I cost me almost a week to recover a system, when updating a 12.04 server, which in case lead to an update on Ubuntu 13.04 which was not intended! | ||
| + | |||
| + | But, after doing a lot of updates on my zentyal installations and reading about the facts, I can agree with the decission of Zentyal going this way. They are getting rid of parts, which can be dealed easily whith native system tools. They focus on networking (firewall), gateway, office and open change as an exchange server replacement. I think, this is a good way - however no easy way for users of the ''commiunity version'' of zentyal. | ||
| + | |||
| + | === Troubleshooting when uninstalling or reinstalling an old zentyal installation === | ||
| + | ==== Prerequesites: ==== | ||
| + | # Check if the zentyal database is installed correctly | ||
| + | # ALWAYS only install one module per time, configure it correctly and then head on! | ||
| + | # Backup your zentyal settings | ||
| + | ==== Possible use cases: ==== | ||
| + | 1. '''Database''' was accidentilly dropped and '''zentyal-core could not be uninstalled / installed'' with the postinstallation script (also see section 3.). So create an empty one ;-) | ||
| + | |||
| + | mysql> create database zentyal; | ||
| + | |||
| + | If you need a new zentyal database, then set the root mysql password: | ||
| + | |||
| + | vim /var/lib/zentyal/conf/zentyal-mysql.passwd | ||
| + | |||
| + | and install a new db: | ||
| + | |||
| + | /usr/share/zentyal/create-db | ||
| + | |||
| + | then restart mysql | ||
| + | |||
| + | service mysql restart | ||
| + | |||
| + | 2. See - if you installed zentyal - that no '''process is running using ebox''': | ||
| + | |||
| + | > ps x | grep ebox | ||
| + | 22871 ? Ss 0:00 sudo -u ebox /usr/bin/redis-server /var/lib/zentyal/conf/redis.conf | ||
| + | |||
| + | 3. A '''postinstallation script''' of a zentyal package, e.g. '''zentyal-core''' is not working, so teh package zentyal-core cannot be conigured or installed: | ||
| + | |||
| + | * Solution: Edit the script standalone and add an ''set -x'', then check for the error messages! | ||
| + | vim /var/lib/dpkg/info/zentyal-core.postinst | ||
| + | #!/bin/bash | ||
| + | set -x | ||
| + | |||
| + | set -e | ||
| + | [...] | ||
| + | |||
| + | * It might be necessary to deactivate the script: | ||
| + | |||
| + | vim /var/lib/dpkg/info/zentyal-core.postinst | ||
| + | |||
| + | #!/bin/bash | ||
| + | exit 0 | ||
| + | |||
| + | set -e | ||
| + | [...] | ||
| + | |||
| + | * re-run dpkg: | ||
| + | |||
| + | dpkg --configure -a | ||
| + | |||
| + | * continue with the web interface, which should be run now! | ||
| + | |||
| + | service zentyal webadmin restart | ||
| + | |||
| + | == Base installation on ubuntu 12.04 LTS == | ||
| + | |||
| + | We are startigng with a bare ubuntu system with only ssh enabled. | ||
| + | |||
| + | First of all please update all packages and do some configurations: | ||
| + | |||
| + | vim /etc/apt/sources.list | ||
| + | |||
| + | Uncomment the following line: | ||
| + | deb http://archive.canonical.com/ubuntu precise partner | ||
| + | |||
| + | We install the '''apt-add-repository'''-script to be able to use the zentyal repository afterwards and do a full system upgrade: | ||
| + | |||
| + | apt-get install -y python-software-properties | ||
| + | apt-add-repository ppa:zentyal/3.2 # PUT THE ACTUAL VERSION NUMBER HERE! | ||
| + | apt-get update | ||
| + | apt-get dist-upgrade | ||
| + | apt-get clean | ||
| + | |||
| + | Then add an administrative account for zentyal. | ||
| + | |||
| + | To be able to access the webinterface you have setup an administrativ user which belongs to the ''admin'' group. This is NOT the ubuntu ''adm'' group! You have to create the group first: | ||
| + | |||
| + | groupadd admin | ||
| + | useradd myAdmin | ||
| + | passwd myAdmin | ||
| + | usermod -G admin -a myAdmin | ||
| + | ... | ||
| + | |||
| + | Pleas verify, that the newly created user is part of the new group with: | ||
| + | |||
| + | su my Admin | ||
| + | groups | ||
| + | |||
| + | Finally reboot the system: | ||
| + | reboot | ||
| + | |||
| + | === Install Zentyal === | ||
| + | The base system then will be install via the command | ||
| + | |||
| + | apt-get -y install zentyal | ||
| + | |||
| + | This will install all prerequisites. | ||
| + | Please prepare to have: | ||
| + | |||
| + | * the or a ''mysql root password'' | ||
| + | * ''the port for the webinterface'' | ||
| + | |||
| + | I suggest 444 for the webinterface, so it would not be in conflict with https-pages on your site (you can then access the webinterface via http://vserver:444). | ||
| + | |||
| + | === Configure the services === | ||
| + | You will now be able to access the webinterface via http://vserver:444. | ||
| + | |||
| + | There choose the services you like. It is always good, of possible to to a snapshot after each of this steps and test, if everything went ok! | ||
| + | |||
| + | |||
| + | === Secure the Webinterface with an ssh tunnel === | ||
| + | This solution to secure the webadmin interface is handy if you are not able to use VPN (e.g. because of a single network card and a kvm virtual guest and no access to the host system). | ||
| + | |||
| + | Tips for the SSH server ( see [1] ): For security reasons configure it to use certificate authenitfication only, which is in fact almost the same like a VPN connection (sshd_config: PasswordAuthentication no, UsePAM no, AllowedUsers special_user, RootLogin no). Use another port - not 22. | ||
| + | Installing Fail2ban is also a good idea! You should generally NOT use the root login for your zentyal server! | ||
| + | |||
| + | Then with you special_user on a local console do: | ||
| + | |||
| + | autossh -L 9000:IP_OF_SERVER:8443 loginname@IP_OF_SERVER | ||
| + | |||
| + | OR | ||
| + | |||
| + | su special_user -c "autossh -L 9000:IP_OF_SERVER:8443 loginname@IP_OF_SERVER" | ||
| + | # autossh keeps the tunnel open, even if it drops | ||
| + | # apt-get install autossh | ||
| + | |||
| + | where | ||
| + | |||
| + | * 8443 is the port of the zentyal web interface | ||
| + | * 9000 is the local port you can access the web interface in your browser | ||
| + | |||
| + | Now you can access the Zentyal Webinterface in your local browser with: | ||
| + | |||
| + | https://localhost:9000 | ||
| + | |||
| + | ''Your Zentyal Webinterface is now save behind public access!'' | ||
| + | |||
| + | [1] Further reading: | ||
| + | * http://askubuntu.com/questions/2271/how-to-harden-an-ssh-server | ||
| + | * https://joscor.com/blog/hardening-openssh-server-ubuntu-14-04/ | ||
| + | * Thread on netcup.de for vserver environment like mine [GER] https://forum.netcup.de/administration-eines-server-vserver/vserver-server-kvm-server/6125-zentyal-vpn-virtuelle-nic-kann-nicht-auf-virtuelle-netzwerkkarte-von-vpn-client-auf-port-x-zugreifen/ | ||
| + | * Thread on zentyal forum [EN] https://forum.zentyal.org/index.php/topic,20028.msg98671.html#msg98671 | ||
| + | |||
| + | == Firewall == | ||
| + | IMPORTANT: Alter your firewall settings to enable the Zentyal administration !!! | ||
| + | |||
| + | Otherwise you won't be able to access the webinterface. | ||
| + | |||
| + | In case you forget this you can temporaryly disable the firewall via commandline and alter this settings. | ||
| + | /etc/init.d/zentyal firewall stop | ||
| + | |||
| + | === Using hooks === | ||
| + | When the firewall module of Zentyal is restarted, all iptable-rules (see [[NAT]]) will be reset. So it is wise to use the zentyal hook system to reset the desired rules! A detailed explanation you'll find here: [[Zentyal#Customization]] | ||
| + | |||
| + | === LDAP port changed on Zentyal 3.2 === | ||
| + | By default LDAP uses the port 389. The problem is, ''that samba4'' - which is part of Zentyal 3.2 - already uses this port. | ||
| + | |||
| + | '''For that reason LDAP on Zentyal 3.x is running on port 390'''. This is not documented on the first sight, and in the firewall, the "LDAP" is assigned to prot 389. | ||
| + | |||
| + | Solution: | ||
| + | # add a custom '''port 390''' and name it e.g. ''LDAP-Zentyal'' | ||
| + | # open the port in the firewall for the internal network traffice (or outside, which is NOT wise) | ||
| + | |||
| + | Test with. Replace <ZENTYAL-SERVER-IP> with the IP of your LDAP-server | ||
| + | ldapsearch -x -p 390 -LLL -h <ZENTYAL-SERVER-IP> -b "" -s base "(objectclass=*)" supportedSASLMechanisms | ||
| + | |||
| + | == Radius == | ||
| + | |||
| + | #/bin/bash | ||
| + | # | ||
| + | # Put this in /etc/rc.local | ||
| + | # | ||
| + | # Monitor zentyal radius | ||
| + | |||
| + | # Upon update, links for freeradius will be set again, so remove them | ||
| + | update-rc.d -f freeradius remove | ||
| + | |||
| + | restart_radius() { | ||
| + | /usr/sbin/service zentyal radius stop | ||
| + | sleep 2 | ||
| + | /usr/bin/killall freeradius | ||
| + | |||
| + | /usr/sbin/service zentyal radius start | ||
| + | } | ||
| + | |||
| + | while (true) | ||
| + | do | ||
| + | if radtest radtestuser 123-qwe localhost 1812 123-qwe | ||
| + | then | ||
| + | echo "RADIUS OK" | ||
| + | |||
| + | else | ||
| + | logger "ERROR: ZENTYAL RADIUS is DOWN ... restarting ..." | ||
| + | restart_radius | ||
| + | fi | ||
| + | |||
| + | sleep 15 | ||
| + | |||
| + | done | ||
| + | |||
| + | == LDAP == | ||
| + | [Update] --[[User:Apos|Apos]] ([[User talk:Apos|talk]]) 11:06, 2 November 2013 (CET) | ||
| + | |||
| + | For Zentyal > 3.5 use port 389, < version 3.5 use prot 390 (!): | ||
| + | |||
| + | root@zentyal:~# ldapsearch -x -p 389 -LLL -h localhost -b "" -s base "(objectclass=*)" supportedSASLMechanisms dn | ||
| + | dn: | ||
| + | supportedSASLMechanisms: GSS-SPNEGO | ||
| + | supportedSASLMechanisms: GSSAPI | ||
| + | supportedSASLMechanisms: NTLM | ||
| + | |||
| + | ldapsearch -x -h localhost -D "testuser@zentyaldomain.sld" -W-b "cn=users,dc=zentyaldomain,dc=sld" -s sub "(cn=*)" cn mail sn | ||
| + | |||
| + | |||
| + | === Redmine === | ||
| + | |||
| + | This is tested with Zentyal 3.2 on Ubuntu 12.04 LTS and [[Redmine|Redmine 2.3.3-2 (via ppa)]]. | ||
| + | ! Be aware and read the section [[Zentyal#Firewall|LDAP port changed on Zentyal 3.2 ]]! | ||
| + | |||
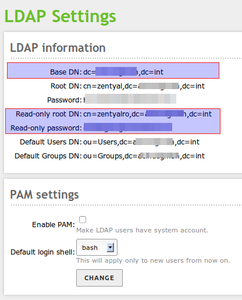
| + | On the ''users and group''-page in the zentyal administration page there are the credentials you need to get '''readonly''' access to LDAP. | ||
| + | |||
| + | <gallery widths=300px heights=300px perrow=2> | ||
| + | Image:Zentyal LDAP Settings I.png|LDAP Settings | ||
| + | Image:Zentyal LDAP Settings II.png|Zentyal LDAP credentials | ||
| + | </gallery> | ||
| + | |||
| + | LDAP credentials in zentyal: | ||
| + | '''Basedomain (Base DN): dc=your_domain,dc=your_tld''' | ||
| + | Rootdomain (Root DN): cn=zentyal,dc=your_domain,dc=your_tld | ||
| + | Password: <admin_secret_pass> | ||
| + | '''Read-only root DN: cn=zentyalro,dc=your_domain,dc=your_tld''' | ||
| + | '''Read-only password: <ro_secret_pass>''' | ||
| + | Default Users DN: ou=Users,dc=your_domain,dc=your_tld | ||
| + | Default Groups DN: ou=Groups,dc=your_domain,dc=your_tld | ||
| + | |||
| + | For testing, if you have the right credential, you can use e.g. the free and opensource [http://jxplorer.org JXplorer] or the commandline: | ||
| + | |||
| + | Check if, the server accepts incoming port | ||
| + | telnet <IP_OF_LDAP_SERVER> 390 | ||
| + | |||
| + | |||
| + | ldapsearch -x -p 390 -b '''"<Basedomain (Base DN)>"''' -h '''<IP_OF_LDAP_SERVER>''' \ | ||
| + | -D '''"<Read-only root DN>"''' -w "<Read-only password>" | ||
| + | |||
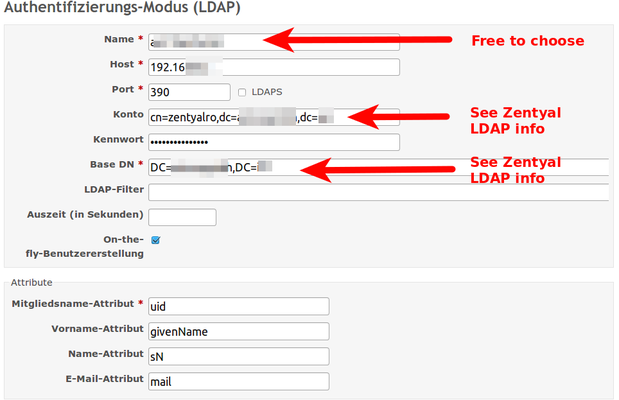
| + | Figured that out, you can e.g. use LDAP in Redmine like this: | ||
| + | <gallery widths=800px heights=400px perrow=2> | ||
| + | Image:Redmine LDAP Zentyal.png |Redmine LDAP settings | ||
| + | </gallery> | ||
| + | |||
| + | === Owncloud === | ||
| + | See [[Owncloud#Owncloud.2C_LDAP_and_Zentyal]]. | ||
| + | |||
| + | And the thread here: | ||
| + | * https://forum.zentyal.org/index.php/topic,23844.new.html#new | ||
| + | |||
| + | === PfSense === | ||
| + | Works with Zentyal 3.4x via Port 389. | ||
| + | |||
| + | And finally (01/2016) works with Zentyal 4.2: | ||
| + | |||
| + | * https://www.wildcardcorp.com/blog/pfsense-and-users-from-zentyal-4-0-over-ldaps | ||
| + | * https://forum.zentyal.org/index.php?topic=23784.0 | ||
| + | |||
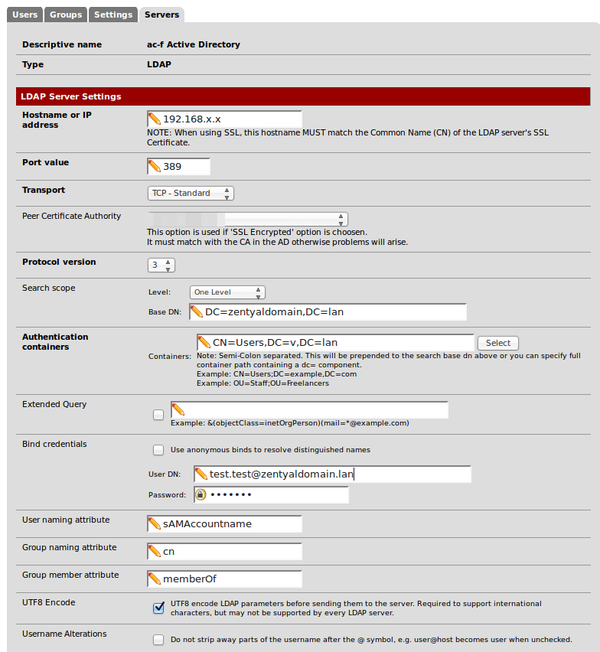
| + | For '''login credentials''' you have to use something like ''someuser@zentyaldomain.lan'' and NOT something like ''CN=Users,DC=...''. | ||
| + | |||
| + | In the following pictures for testing purpose I created the user "test.test" within zentyal. But you can use any user you like to get a readonly access to ldap. | ||
| + | |||
| + | '''LDAP at port 389:''' | ||
| + | |||
| + | [[File:Pfsense22 ldap zentyal42.png|600px]] | ||
| + | |||
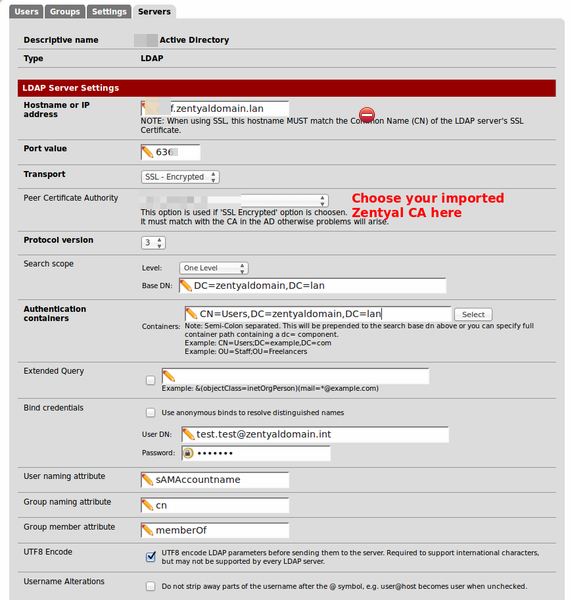
| + | '''LDAPS at port 686''' | ||
| + | |||
| + | For ldap'''s''':// you have to import the zentyal certificate into pfsense. | ||
| + | |||
| + | To get these data the easiest way is to log into your zentyal domain controller do: | ||
| + | |||
| + | openssl s_client -showcerts -connect localhost:636 | ||
| + | |||
| + | Then copy the certificate data. Open the '''cert manager''' within pfsense webinterface and create '''(import) a new CA''' using this certificate (paste it into the public key section). | ||
| + | |||
| + | When configuring the server: you have to use the ''full qualified domain name'' for the server address, not the IP if you are using ssl: | ||
| + | |||
| + | Also see: | ||
| + | * https://www.wildcardcorp.com/blog/pfsense-and-users-from-zentyal-4-0-over-ldaps | ||
| + | |||
| + | |||
| + | [[File:Pfsense22 ldaps zentyal42.png|600px]] | ||
| + | |||
| + | == Network == | ||
| + | Zentyal completely cares for the network on your ubuntu server. | ||
| + | |||
| + | Therefore you should - but do not have to - '''disable the network-manager''': | ||
| + | |||
| + | sudo service network-manager stop | ||
| + | |||
| + | Create an override file for the upstart job: | ||
| + | |||
| + | echo "manual" | sudo tee /etc/init/network-manager.override | ||
| + | |||
| + | Then configure your network cards with zentyal and be sure to enable the WAN switch, if you are using zentyal on an internetserver without a gateway in front of it, that is, if your server ip is an internet ip address: | ||
| + | |||
| + | [[File:20131006 Zentyal Network 1.png|600px]] | ||
| + | |||
| + | == VPN == | ||
| + | A good guide: | ||
| + | * https://pricklytech.wordpress.com/2011/03/24/ubuntu-server-installing-and-configuring-zentyal-openvpn/ | ||
| + | |||
| + | On a kvm based vserver (netcup.de) check, if the following configurations are enabled: | ||
| + | |||
| + | Enable ip_forward: | ||
| + | echo "1" > /proc/sys/net/ipv4/ip_forward | ||
| + | |||
| + | Forward tap0: | ||
| + | iptables -A FORWARD -i eth0 -o tap0 -m state --state RELATED,ESTABLISHED -j ACCEPT | ||
| + | iptables -A FORWARD -i tap0 -o eth0 -j ACCEPT | ||
| + | |||
| + | or tun0, if you are using tun: | ||
| + | iptables -A FORWARD -i eth0 -o tun0 -m state --state RELATED,ESTABLISHED -j ACCEPT | ||
| + | iptables -A FORWARD -i tun0 -o eth0 -j ACCEPT | ||
| + | |||
| + | '''BUT:''' this won't work in a virtual guest (vserver) due to NAT: | ||
| + | * see: https://forum.zentyal.org/index.php/topic,20028.msg98671.html#msg98671 ). To '''secure the webinterface''' you should use the method pointed out in this article and / or the section above: [[#Secure_the_Webinterface_with_an_ssh_tunnel]]. | ||
| + | |||
| + | == Mail == | ||
| + | First of all we like to install an e-mail-system. This is what most users want, when they install zentyal on an vserver. | ||
| + | |||
| + | If you only choose the mail plugin, several plugins will be installed, too: | ||
| + | |||
| + | [[File:Zentyal mail 1.png|600px]] | ||
| + | |||
| + | In the next steps, it is important that you | ||
| + | |||
| + | # choose eth0 as interface (see picture) and later | ||
| + | # ''DHCP'' for the configuration of eth0. | ||
| + | # Directly afterwards you will be asked for the Kerberos REALM. Please use the domain name of your server, if configured. If not SKIP this step for now! | ||
| + | |||
| + | [[File:Zeentyal Mail 2.png|600px]] | ||
| + | |||
| + | == Virtualisation module moved == | ||
| + | Like advised here ... | ||
| + | * http://forum.zentyal.org/index.php/topic,17931.0.html | ||
| + | |||
| + | ... some of the modules - especially the virtualisation module - have moved to a so called contribution section. | ||
| + | |||
| + | : '' [...] | ||
| + | : ''Moreover, as announced in the Forum, the following modules have been moved to the contrib repositories in order to live | ||
| + | : ''up to our motto of being an easy-to-use Linux small business server: | ||
| + | : ''* PPTP | ||
| + | : ''* Virtualization | ||
| + | : ''* Thin clients | ||
| + | : ''* VoIP | ||
| + | : '' [...] | ||
| + | |||
| + | A solution can be found here: | ||
| + | |||
| + | * http://forum.zentyal.org/index.php/topic,18342.0.html | ||
| + | |||
| + | == Customization == | ||
| + | A Zentyal system can be adopted to your own needs in a very easy way: using hooks! | ||
| + | |||
| + | Every service on a Linux system is configured in its own configuration file. Mostly living in ''/etc/...''. Zentyal stores the setting of all services in so called "stubs". These templates can be overridden using hooks. | ||
| + | |||
| + | But using hooks make the system more complex. This means: when doing '''updates''' of your zentyal system, you have to be careful and integrate actual changes of zentyal's stub into your own hook. Your own hooks are not updated automatically as well. | ||
| + | |||
| + | How this is done: | ||
| + | * [http://www.youtube.com/user/zentyal Youtube Zentyal channel] | ||
| + | * [https://wiki.zentyal.org/wiki/En/4.0/Appendix_B:_Development_and_advanced_configuration] | ||
| + | |||
| + | Also see the section [[Zentyal#Firewall]]. | ||
| + | |||
| + | == Samba4 - changing the REALM == | ||
| + | |||
| + | Sometimes it can be necessary to alter the realm (kerberos). This will brake all user related modules and forces them to reinstall: | ||
/usr/share/zentyal-users/reinstall | /usr/share/zentyal-users/reinstall | ||
| + | |||
| + | # Then klick on the "Ally"-Button on the upper right corner of the web-interface. | ||
| + | # Then go to "Users" -> "Mode...", change the realm and apply. | ||
| + | # Then you have to reenable the "Users"-module and apply the changes. | ||
| + | # Then you can also reenable the "Samba"-module and apply the changes. | ||
see: http://trac.zentyal.org/ticket/5695 | see: http://trac.zentyal.org/ticket/5695 | ||
| + | |||
| + | == Openchange == | ||
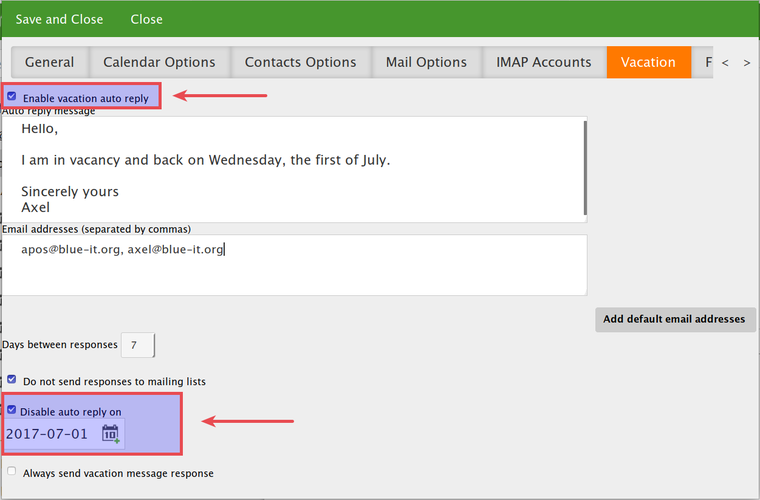
| + | === Enable the vacation plugin === | ||
| + | * read about altering stubs: https://wiki.zentyal.org/wiki/En/3.5/Development_and_advanced_configuration#Stubs | ||
| + | |||
| + | 1. Create a new stubs directory in '/etc/zentyal' | ||
| + | mkdir -p mkdir -p /etc/zentyal/stubs/openchange/ | ||
| + | |||
| + | 2. Copy over the standard stub for openchange to the newly created directory | ||
| + | cp /usr/share/zentyal/stubs/openchange/sogo.conf.mas /etc/zentyal/stubs/openchange/ | ||
| + | |||
| + | 3. Change the sieve plugin configuration | ||
| + | vim /etc/zentyal/stubs/openchange/sogo.conf.mas | ||
| + | |||
| + | /* Sieve configuration */ | ||
| + | /* SOGoVacationEnabled = NO; */ | ||
| + | SOGoVacationEnabled = YES; | ||
| + | [...] | ||
| + | |||
| + | 4. Restart openchange service | ||
| + | service zentyal openchange restart | ||
| + | * Restarting Zentyal module: openchange [ OK ] | ||
| + | |||
| + | 5. The plugin is visible now in your email preferences as a new button ("vacation" in English). | ||
| + | |||
| + | <gallery widths=800px heights=180px perrow=2> | ||
| + | Image:Openchange vacation plugin 01.png | New button | ||
| + | </gallery> | ||
| + | |||
| + | <gallery widths=800px heights=500px perrow=2> | ||
| + | Image:Openchange vacation 02.png | Configuration | ||
| + | </gallery> | ||
| + | |||
| + | Thanks: https://forum.zentyal.org/index.php?topic=25649.0 | ||
| + | |||
| + | === Reprovisioning fails === | ||
| + | |||
| + | [4.2] The HACK promoted hier Worked for me in nZentyal 4.2 on Ubuntu 14.04 (June 2016) to reprovision Openchange after enabling / reenabling the module: | ||
| + | |||
| + | * https://forum.zentyal.org/index.php/topic,24625.msg94859.html#msg94859 - Post 13 | ||
| + | |||
| + | vim /usr/lib/python2.7/dist-packages/openchange/provision.py +466 | ||
| + | |||
| + | |||
| + | add the line schemas = [] | ||
| + | 'description': 'Extend existing Samba classes and attributes', | ||
| + | 'modify_mode': True}] | ||
| + | |||
| + | '''schemas = []''' | ||
| + | |||
| + | for schema in schemas: | ||
| + | try: | ||
| + | |||
| + | [4.0] Worked for me in 2015 | ||
| + | |||
| + | * https://forum.zentyal.org/index.php?topic=24625.0 | ||
| + | |||
| + | In my case it helped to alter the call of the provisioning call and add ''"--ignore-already-exists"'' into the line: | ||
| + | |||
| + | vim /usr/share/perl5/EBox/OpenChange/Model/Provision.pm +457 | ||
| + | |||
| + | try { | ||
| + | my $cmd = "openchange_provision '''--ignore-already-exists''' --firstorg='$organizationName' "; | ||
| + | |||
| + | |||
| + | Another | ||
| + | |||
| + | === Active sync === | ||
| + | |||
| + | Read carefully the section about Active sync ... | ||
| + | * https://wiki.zentyal.org/wiki/En/4.1/OpenChange_%28Microsoft%28R%29_Exchange_Server_protocol_implementation%29 | ||
| + | |||
| + | ... and you will see you have to install manually ... | ||
| + | |||
| + | sudo apt-get install sogo-activesync | ||
| + | |||
| + | ... to get the choice on the Openchange site. | ||
| + | |||
| + | === Samba 4 error === | ||
| + | If yout get the error: | ||
| + | |||
| + | > Could not get ticket: could not acquire credentials using an initial credentials context: Password has expired | ||
| + | |||
| + | See: | ||
| + | * https://forum.zentyal.org/index.php?topic=24210.0 | ||
| + | |||
| + | sudo samba-tool user setexpiry administrator --noexpiry | ||
| + | |||
| + | The same applies to mail module | ||
| + | > Could not get ticket: could not acquire credentials using an initial credentials context: No ENC-TS found | ||
| + | |||
| + | == Monitoring Services == | ||
| + | |||
| + | === Apache === | ||
| + | With e.g. monit: see [[Server_Monitoring#Zentyal_Apache2]]. | ||
| + | |||
| + | === Radius === | ||
| + | There seems to be a problem with freeradius and Zentyal 3.4. | ||
| + | |||
| + | update-alternatives -f freeradius remove | ||
| + | |||
| + | vim ~/bin/monitor_zentyal_radius | ||
| + | |||
| + | |||
| + | # !/bin/bash | ||
| + | |||
| + | # Monitor radius | ||
| + | |||
| + | restart_radius() { | ||
| + | /usr/sbin/service zentyal radius stop | ||
| + | sleep 2 | ||
| + | /usr/bin/killall freeradius | ||
| + | |||
| + | /usr/sbin/service zentyal radius start | ||
| + | } | ||
| + | |||
| + | while (true) | ||
| + | do | ||
| + | if radtest radtestuser 123-qwe localhost 1812 123-qwe | ||
| + | then | ||
| + | echo "RADIUS OK" | ||
| + | |||
| + | else | ||
| + | logger "ERROR: ZENTYAL RADIUS is DOWN ... restarting ..." | ||
| + | restart_radius | ||
| + | fi | ||
| + | |||
| + | sleep 15 | ||
| + | |||
| + | done | ||
| + | |||
| + | == Docker == | ||
| + | |||
| + | No solution yet: posted a thread in the zentyal forum and started investigations into the subject. See: | ||
| + | |||
| + | * https://forum.zentyal.org/index.php/topic,25020.msg101618.html#msg101618 | ||
| + | |||
| + | Also see [[Docker]] for basic docker informations on Ubuntu. | ||
[[Category: Zentyal]] | [[Category: Zentyal]] | ||
Latest revision as of 14:30, 19 September 2017
Contents
[hide]- 1 Zentyal - the small business server for Linux
- 1.1 Important links
- 1.2 Installation and Upgrading to Ubuntu 14.04 LTS
- 1.3 Base installation on ubuntu 12.04 LTS
- 1.4 Firewall
- 1.5 Radius
- 1.6 LDAP
- 1.7 Network
- 1.8 VPN
- 1.9 Mail
- 1.10 Virtualisation module moved
- 1.11 Customization
- 1.12 Samba4 - changing the REALM
- 1.13 Openchange
- 1.14 Monitoring Services
- 1.15 Docker
Zentyal - the small business server for Linux
Important links
- http://wiki.ubuntuusers.de/Zentyal
- http://wiki.ubuntuusers.de/Zentyal/PPA-Installation
- http://ubuntuserverguide.com/2012/11/how-to-instal-zentyal-3-0-on-ubuntu-server-12-04-lts.html
Installation and Upgrading to Ubuntu 14.04 LTS
HowTo
Unfortunately Zentyal changed it's release policy DRAMATICALLY since Version 3.4 (3.5).
- See and carfully read: Zentyal Release Policy.
- 3.3 roadmap
- 3.4 roadmap
- 4.0 roadmap
Nur die kommerziellen Versionen Zentyal folgen den Ubuntu-LTS Fahrplan und bieten entsprechende Migrationswege und Werkzeuge an!
Be very carful on updating an existing Ubuntu 12.04 LTS Zentyal installation.
You will most probably loose a lot of important functionality!
Read carfully and check the new requirements at http://www.zentyal.org/zentyal-release-policy
It in fact boils down that you loose on update:
- Zarafa module (!) - and thereby your mail configuration an installation which ist WORST!
- Webserver configuration module - you have to manage it manually. This is not very dramatic.
- Be aware and prepared of apache2.4 versus apache 2.2 config changes (which mainly you can read about in Webserver#Apache_2.4).
- Radius - which in my case is crucial, since almost any service relys on this for authentification!
New is:
- Openchange support - which is very PROMISING
- You'll get an Rolling Release - that means updating Zentyal almost ever need updating the server to a new Ubuntu version which could probably lead to strange side effects for other mission critical systems (database server, programming language environments like ruby) ...
A personal comment on this
As far as I can say, the new release policy of Zentyal is very annoying on the first place. I cost me almost a week to recover a system, when updating a 12.04 server, which in case lead to an update on Ubuntu 13.04 which was not intended!
But, after doing a lot of updates on my zentyal installations and reading about the facts, I can agree with the decission of Zentyal going this way. They are getting rid of parts, which can be dealed easily whith native system tools. They focus on networking (firewall), gateway, office and open change as an exchange server replacement. I think, this is a good way - however no easy way for users of the commiunity version of zentyal.
Troubleshooting when uninstalling or reinstalling an old zentyal installation
Prerequesites:
- Check if the zentyal database is installed correctly
- ALWAYS only install one module per time, configure it correctly and then head on!
- Backup your zentyal settings
Possible use cases:
1. Database' was accidentilly dropped and zentyal-core could not be uninstalled / installed with the postinstallation script (also see section 3.). So create an empty one ;-)
mysql> create database zentyal;
If you need a new zentyal database, then set the root mysql password:
vim /var/lib/zentyal/conf/zentyal-mysql.passwd
and install a new db:
/usr/share/zentyal/create-db
then restart mysql
service mysql restart
2. See - if you installed zentyal - that no process is running using ebox:
> ps x | grep ebox 22871 ? Ss 0:00 sudo -u ebox /usr/bin/redis-server /var/lib/zentyal/conf/redis.conf
3. A postinstallation script of a zentyal package, e.g. zentyal-core is not working, so teh package zentyal-core cannot be conigured or installed:
- Solution: Edit the script standalone and add an set -x, then check for the error messages!
vim /var/lib/dpkg/info/zentyal-core.postinst #!/bin/bash set -x set -e [...]
- It might be necessary to deactivate the script:
vim /var/lib/dpkg/info/zentyal-core.postinst
#!/bin/bash exit 0 set -e [...]
- re-run dpkg:
dpkg --configure -a
- continue with the web interface, which should be run now!
service zentyal webadmin restart
Base installation on ubuntu 12.04 LTS
We are startigng with a bare ubuntu system with only ssh enabled.
First of all please update all packages and do some configurations:
vim /etc/apt/sources.list
Uncomment the following line:
deb http://archive.canonical.com/ubuntu precise partner
We install the apt-add-repository-script to be able to use the zentyal repository afterwards and do a full system upgrade:
apt-get install -y python-software-properties apt-add-repository ppa:zentyal/3.2 # PUT THE ACTUAL VERSION NUMBER HERE! apt-get update apt-get dist-upgrade apt-get clean
Then add an administrative account for zentyal.
To be able to access the webinterface you have setup an administrativ user which belongs to the admin group. This is NOT the ubuntu adm group! You have to create the group first:
groupadd admin useradd myAdmin passwd myAdmin usermod -G admin -a myAdmin ...
Pleas verify, that the newly created user is part of the new group with:
su my Admin groups
Finally reboot the system:
reboot
Install Zentyal
The base system then will be install via the command
apt-get -y install zentyal
This will install all prerequisites. Please prepare to have:
- the or a mysql root password
- the port for the webinterface
I suggest 444 for the webinterface, so it would not be in conflict with https-pages on your site (you can then access the webinterface via http://vserver:444).
Configure the services
You will now be able to access the webinterface via http://vserver:444.
There choose the services you like. It is always good, of possible to to a snapshot after each of this steps and test, if everything went ok!
Secure the Webinterface with an ssh tunnel
This solution to secure the webadmin interface is handy if you are not able to use VPN (e.g. because of a single network card and a kvm virtual guest and no access to the host system).
Tips for the SSH server ( see [1] ): For security reasons configure it to use certificate authenitfication only, which is in fact almost the same like a VPN connection (sshd_config: PasswordAuthentication no, UsePAM no, AllowedUsers special_user, RootLogin no). Use another port - not 22. Installing Fail2ban is also a good idea! You should generally NOT use the root login for your zentyal server!
Then with you special_user on a local console do:
autossh -L 9000:IP_OF_SERVER:8443 loginname@IP_OF_SERVER
OR
su special_user -c "autossh -L 9000:IP_OF_SERVER:8443 loginname@IP_OF_SERVER" # autossh keeps the tunnel open, even if it drops # apt-get install autossh
where
- 8443 is the port of the zentyal web interface
- 9000 is the local port you can access the web interface in your browser
Now you can access the Zentyal Webinterface in your local browser with:
https://localhost:9000
Your Zentyal Webinterface is now save behind public access!
[1] Further reading:
- http://askubuntu.com/questions/2271/how-to-harden-an-ssh-server
- https://joscor.com/blog/hardening-openssh-server-ubuntu-14-04/
- Thread on netcup.de for vserver environment like mine [GER] https://forum.netcup.de/administration-eines-server-vserver/vserver-server-kvm-server/6125-zentyal-vpn-virtuelle-nic-kann-nicht-auf-virtuelle-netzwerkkarte-von-vpn-client-auf-port-x-zugreifen/
- Thread on zentyal forum [EN] https://forum.zentyal.org/index.php/topic,20028.msg98671.html#msg98671
Firewall
IMPORTANT: Alter your firewall settings to enable the Zentyal administration !!!
Otherwise you won't be able to access the webinterface.
In case you forget this you can temporaryly disable the firewall via commandline and alter this settings.
/etc/init.d/zentyal firewall stop
Using hooks
When the firewall module of Zentyal is restarted, all iptable-rules (see NAT) will be reset. So it is wise to use the zentyal hook system to reset the desired rules! A detailed explanation you'll find here: Zentyal#Customization
LDAP port changed on Zentyal 3.2
By default LDAP uses the port 389. The problem is, that samba4 - which is part of Zentyal 3.2 - already uses this port.
For that reason LDAP on Zentyal 3.x is running on port 390. This is not documented on the first sight, and in the firewall, the "LDAP" is assigned to prot 389.
Solution:
- add a custom port 390 and name it e.g. LDAP-Zentyal
- open the port in the firewall for the internal network traffice (or outside, which is NOT wise)
Test with. Replace <ZENTYAL-SERVER-IP> with the IP of your LDAP-server
ldapsearch -x -p 390 -LLL -h <ZENTYAL-SERVER-IP> -b "" -s base "(objectclass=*)" supportedSASLMechanisms
Radius
#/bin/bash
#
# Put this in /etc/rc.local
#
# Monitor zentyal radius
# Upon update, links for freeradius will be set again, so remove them
update-rc.d -f freeradius remove
restart_radius() {
/usr/sbin/service zentyal radius stop
sleep 2
/usr/bin/killall freeradius
/usr/sbin/service zentyal radius start
}
while (true)
do
if radtest radtestuser 123-qwe localhost 1812 123-qwe
then
echo "RADIUS OK"
else
logger "ERROR: ZENTYAL RADIUS is DOWN ... restarting ..."
restart_radius
fi
sleep 15
done
LDAP
[Update] --Apos (talk) 11:06, 2 November 2013 (CET)
For Zentyal > 3.5 use port 389, < version 3.5 use prot 390 (!):
root@zentyal:~# ldapsearch -x -p 389 -LLL -h localhost -b "" -s base "(objectclass=*)" supportedSASLMechanisms dn
dn:
supportedSASLMechanisms: GSS-SPNEGO supportedSASLMechanisms: GSSAPI supportedSASLMechanisms: NTLM
ldapsearch -x -h localhost -D "testuser@zentyaldomain.sld" -W-b "cn=users,dc=zentyaldomain,dc=sld" -s sub "(cn=*)" cn mail sn
Redmine
This is tested with Zentyal 3.2 on Ubuntu 12.04 LTS and Redmine 2.3.3-2 (via ppa). ! Be aware and read the section LDAP port changed on Zentyal 3.2 !
On the users and group-page in the zentyal administration page there are the credentials you need to get readonly access to LDAP.
LDAP credentials in zentyal:
Basedomain (Base DN): dc=your_domain,dc=your_tld Rootdomain (Root DN): cn=zentyal,dc=your_domain,dc=your_tld Password: <admin_secret_pass> Read-only root DN: cn=zentyalro,dc=your_domain,dc=your_tld Read-only password: <ro_secret_pass> Default Users DN: ou=Users,dc=your_domain,dc=your_tld Default Groups DN: ou=Groups,dc=your_domain,dc=your_tld
For testing, if you have the right credential, you can use e.g. the free and opensource JXplorer or the commandline:
Check if, the server accepts incoming port
telnet <IP_OF_LDAP_SERVER> 390
ldapsearch -x -p 390 -b "<Basedomain (Base DN)>" -h <IP_OF_LDAP_SERVER> \ -D "<Read-only root DN>" -w "<Read-only password>"
Figured that out, you can e.g. use LDAP in Redmine like this:
Owncloud
See Owncloud#Owncloud.2C_LDAP_and_Zentyal.
And the thread here:
PfSense
Works with Zentyal 3.4x via Port 389.
And finally (01/2016) works with Zentyal 4.2:
- https://www.wildcardcorp.com/blog/pfsense-and-users-from-zentyal-4-0-over-ldaps
- https://forum.zentyal.org/index.php?topic=23784.0
For login credentials you have to use something like someuser@zentyaldomain.lan and NOT something like CN=Users,DC=....
In the following pictures for testing purpose I created the user "test.test" within zentyal. But you can use any user you like to get a readonly access to ldap.
LDAP at port 389:
LDAPS at port 686
For ldaps:// you have to import the zentyal certificate into pfsense.
To get these data the easiest way is to log into your zentyal domain controller do:
openssl s_client -showcerts -connect localhost:636
Then copy the certificate data. Open the cert manager within pfsense webinterface and create (import) a new CA using this certificate (paste it into the public key section).
When configuring the server: you have to use the full qualified domain name for the server address, not the IP if you are using ssl:
Also see:
* https://www.wildcardcorp.com/blog/pfsense-and-users-from-zentyal-4-0-over-ldaps
Network
Zentyal completely cares for the network on your ubuntu server.
Therefore you should - but do not have to - disable the network-manager:
sudo service network-manager stop
Create an override file for the upstart job:
echo "manual" | sudo tee /etc/init/network-manager.override
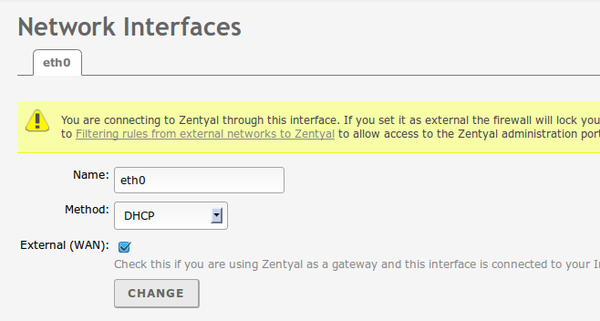
Then configure your network cards with zentyal and be sure to enable the WAN switch, if you are using zentyal on an internetserver without a gateway in front of it, that is, if your server ip is an internet ip address:
VPN
A good guide:
On a kvm based vserver (netcup.de) check, if the following configurations are enabled:
Enable ip_forward:
echo "1" > /proc/sys/net/ipv4/ip_forward
Forward tap0:
iptables -A FORWARD -i eth0 -o tap0 -m state --state RELATED,ESTABLISHED -j ACCEPT iptables -A FORWARD -i tap0 -o eth0 -j ACCEPT
or tun0, if you are using tun:
iptables -A FORWARD -i eth0 -o tun0 -m state --state RELATED,ESTABLISHED -j ACCEPT iptables -A FORWARD -i tun0 -o eth0 -j ACCEPT
BUT: this won't work in a virtual guest (vserver) due to NAT:
- see: https://forum.zentyal.org/index.php/topic,20028.msg98671.html#msg98671 ). To secure the webinterface you should use the method pointed out in this article and / or the section above: #Secure_the_Webinterface_with_an_ssh_tunnel.
First of all we like to install an e-mail-system. This is what most users want, when they install zentyal on an vserver.
If you only choose the mail plugin, several plugins will be installed, too:
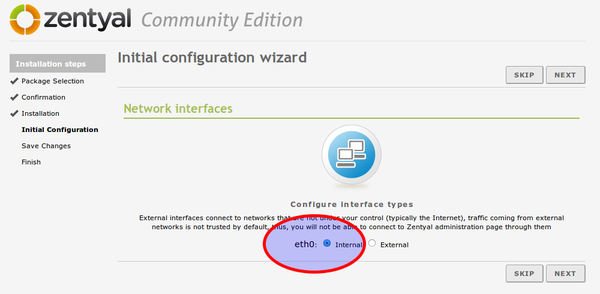
In the next steps, it is important that you
- choose eth0 as interface (see picture) and later
- DHCP for the configuration of eth0.
- Directly afterwards you will be asked for the Kerberos REALM. Please use the domain name of your server, if configured. If not SKIP this step for now!
Virtualisation module moved
Like advised here ...
... some of the modules - especially the virtualisation module - have moved to a so called contribution section.
- [...]
- Moreover, as announced in the Forum, the following modules have been moved to the contrib repositories in order to live
- up to our motto of being an easy-to-use Linux small business server:
- * PPTP
- * Virtualization
- * Thin clients
- * VoIP
- [...]
A solution can be found here:
Customization
A Zentyal system can be adopted to your own needs in a very easy way: using hooks!
Every service on a Linux system is configured in its own configuration file. Mostly living in /etc/.... Zentyal stores the setting of all services in so called "stubs". These templates can be overridden using hooks.
But using hooks make the system more complex. This means: when doing updates of your zentyal system, you have to be careful and integrate actual changes of zentyal's stub into your own hook. Your own hooks are not updated automatically as well.
How this is done:
Also see the section Zentyal#Firewall.
Samba4 - changing the REALM
Sometimes it can be necessary to alter the realm (kerberos). This will brake all user related modules and forces them to reinstall:
/usr/share/zentyal-users/reinstall
- Then klick on the "Ally"-Button on the upper right corner of the web-interface.
- Then go to "Users" -> "Mode...", change the realm and apply.
- Then you have to reenable the "Users"-module and apply the changes.
- Then you can also reenable the "Samba"-module and apply the changes.
see: http://trac.zentyal.org/ticket/5695
Openchange
Enable the vacation plugin
- read about altering stubs: https://wiki.zentyal.org/wiki/En/3.5/Development_and_advanced_configuration#Stubs
1. Create a new stubs directory in '/etc/zentyal'
mkdir -p mkdir -p /etc/zentyal/stubs/openchange/
2. Copy over the standard stub for openchange to the newly created directory
cp /usr/share/zentyal/stubs/openchange/sogo.conf.mas /etc/zentyal/stubs/openchange/
3. Change the sieve plugin configuration vim /etc/zentyal/stubs/openchange/sogo.conf.mas
/* Sieve configuration */ /* SOGoVacationEnabled = NO; */ SOGoVacationEnabled = YES; [...]
4. Restart openchange service
service zentyal openchange restart * Restarting Zentyal module: openchange [ OK ]
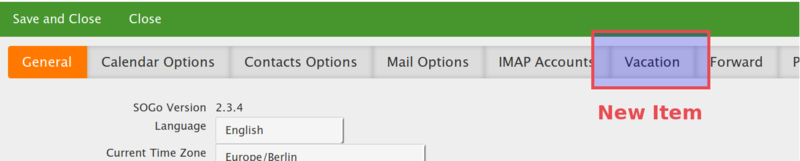
5. The plugin is visible now in your email preferences as a new button ("vacation" in English).
Thanks: https://forum.zentyal.org/index.php?topic=25649.0
Reprovisioning fails
[4.2] The HACK promoted hier Worked for me in nZentyal 4.2 on Ubuntu 14.04 (June 2016) to reprovision Openchange after enabling / reenabling the module:
vim /usr/lib/python2.7/dist-packages/openchange/provision.py +466
add the line schemas = []
'description': 'Extend existing Samba classes and attributes',
'modify_mode': True}]
schemas = []
for schema in schemas:
try:
[4.0] Worked for me in 2015
In my case it helped to alter the call of the provisioning call and add "--ignore-already-exists" into the line:
vim /usr/share/perl5/EBox/OpenChange/Model/Provision.pm +457
try {
my $cmd = "openchange_provision --ignore-already-exists --firstorg='$organizationName' ";
Another
Active sync
Read carefully the section about Active sync ...
... and you will see you have to install manually ...
sudo apt-get install sogo-activesync
... to get the choice on the Openchange site.
Samba 4 error
If yout get the error:
> Could not get ticket: could not acquire credentials using an initial credentials context: Password has expired
See:
sudo samba-tool user setexpiry administrator --noexpiry
The same applies to mail module > Could not get ticket: could not acquire credentials using an initial credentials context: No ENC-TS found
Monitoring Services
Apache
With e.g. monit: see Server_Monitoring#Zentyal_Apache2.
Radius
There seems to be a problem with freeradius and Zentyal 3.4.
update-alternatives -f freeradius remove
vim ~/bin/monitor_zentyal_radius
# !/bin/bash
# Monitor radius
restart_radius() {
/usr/sbin/service zentyal radius stop
sleep 2
/usr/bin/killall freeradius
/usr/sbin/service zentyal radius start
}
while (true)
do
if radtest radtestuser 123-qwe localhost 1812 123-qwe
then
echo "RADIUS OK"
else
logger "ERROR: ZENTYAL RADIUS is DOWN ... restarting ..."
restart_radius
fi
sleep 15
done
Docker
No solution yet: posted a thread in the zentyal forum and started investigations into the subject. See:
Also see Docker for basic docker informations on Ubuntu.